- July 20242
- May 20243
- August 20232
- June 20235
- May 20232
- April 20231
- March 20233
- February 20234
- January 20234
- December 20224
- November 20223
- October 20222
- September 202210
- August 20221
- July 20222
- June 20226
- May 202212
- April 202213
- March 202219
- February 202217
- January 202218
- December 202119
- November 202118
- October 202132
- September 202135
- August 202138
- July 202143
- February 20213
- January 20217
- December 20208
- November 20206
- October 20208
- September 20208
- August 20208
- July 20208
- June 20206
- April 20194
- March 20194
Labels
- Affiliate
- Affiliate Marketing
- Android
- Bitcoin
- blogger Tutorial
- Cashback
- Computer
- Crypto
- Cryptocurrency
- DIY Tutorials
- Earn Money
- Ecommerce
- Email MArketing
- facebook tutorial
- Family
- Gadgets
- Gamer and Console
- Hobbies and skills
- Home and backyard
- Home building
- Home electronics
- Home furnitures
- Home Gardening
- Homework
- House care
- How to
- How to build
- How to write
- infos
- Insurance
- internet
- Internet and security
- internet Marketing
- internet Services
- Investing
- iphone
- KDP Interior Templates
- Life Care
- life Hacks
- Linux Tutorial
- Mac
- make Money
- Online Solutions
- Pet care
- Products Review
- Reviews
- Search Engine
- Security
- SEO
- shopping
- Smart Home
- smartphone
- social media
- Software Tutorial
- SSEO
- Tech Problem
- VPN
- Wallet and Money
- Web Hosting
- Web Tutorials
- Windows
- work
- Work online
- Youtube Review
- Youtube Tutorial
- Youtubers Tutorials
Dealing with visitors links in blogger comments Are you bothered by the links that visitors put inside your blog comments? I will offer you a set of solutions to deal with it without having to delete it. The comments section affects one way or another the arrangement of your blog and the strength of its archiving. We know that one of the simplest ways to bring visits to the site is to publish its link in a group of places, including comments. This strategy is usually beneficial to the comment owner, but it is likely to be harmful to the owner of the site as losing visitors instead of browsing the rest of the content. Perhaps some will ask a question why I do not delete the comments in which the links are manual, the reason is simply that sometimes visitors add comments related to the post and of high quality, but add defamatory links to it, in this case, we do not want to delete all the comment, but we want to hide the link only. I will present to you a set of different scripts, each o...
10 Best Video Editing App For smartphone
with Video Editors Apps you can edit videos for better quality like its brightness, contrast, orientation, or, you'll want to feature something to form the photos look catchy and make it more fantastic. Video content is on the increase . Especially when it involves promoting products to customers. Video editing apps are one among the heaviest tasks that a tool can perform. a touch Video editing can dramatically increase the impact of your film. You might have already got a high-quality camera built into your smartphone, but editing your raw footage and preparing it for publication requires a third-party mobile video editing apps. Best Video Editing App For Android and iphone 1. Adobe Premiere Rush An app which has made a distinct segment for itself within the arena of video editing apps. This too may be a free app which helps you to craft high-quality videos at a really fast rate. This app features a sort of music, effects, and tools which can facilitate in your video editi...
simple way to add drop down list in excel [ step-by-step ]
In this toturial i will show you how to make a drop-down rundown in a Microsoft Excel spreadsheet, utilizing a PC. This element permits you to make a rundown of things to browse, and supplement a drop-down selector into any vacant cell on your spreadsheet. The drop-down component is just accessible on work area forms of Excel. Stage 1: Go to the "Data" tab This progression is simple! Essentially move your cursor to the "Data" tab and snap it. Snap the data tab in the lace. Stage 2: Snap "Data Approval" Presently click the catch "Data approval" in the lace (don't tap the little bolt – just snap the top piece of the catch). Tapping the data approval button on the strip will give you the alternative to make a drop down menu. Stage 3: Pick the "List" In the spring up box, you have to tap the drop-down menu to pick what sort of data approval technique you need to utilize (how meta is that?!). Snap the bolt close to the field and...
قائمة الأكثر شعبية
Best Ways to save electricity at home
Best Ways to save electricity at home Electricity is the basis for all devices in all homes. Without it, many businesses will be disrupted, and electricity is not necessarily used in homes only, but the most use of electricity and its consumption is in the home of each of us. And this is what made most countries suffer from electricity problems, which in turn negatively affected the areas of life and the environment that exist in all societies, so everyone must preserve electricity to benefit from it in the services it provides to us that we desperately need in our daily lives. Electricity : . Electricity is a group of different phenomena resulting from the presence and flow of electric charges, and among these phenomena are static electricity and lightning. . There is also another type of electricity that relies on non-renewable sources, as many countries have resorted to discovering new sources of energy to generate electricity, and among the forms of those sources is oil, but that e...
How to write a monologue in easy steps
Inside monologues are precarious to compose. In this article, you will discover valuable tips on the best way to compose a monolog and improve your script Instructions to Write a Monologue to Advance Your Story Indeed, even the most gifted scholars may battle with specific things when composing their accounts and books or building up their characters. The most well-known issues concern language and spelling yet these things can be handily checked and improved. Additionally, a great deal of issues for the most part emerge with regards to substance or style. To assist you with maintaining a strategic distance from regular mix-up during the creative cycle, we give you composing tips on the most proficient method to compose a monolog given by the accomplished authors from proficient article composing administration. What is Monologue? The monologue is an artistic gadget that is regularly utilized by artists, dramatists, and authors when the speaker or the chara...
Here are 10 of the most important WordPress plugins
Here are 10 of the most important WordPress plugins that every website needs There are many WordPress plugins and many people are always looking for the best plugin for their site, whether to improve SEO, speed up the site, backup, etc. It is worth noting that there are more than 58000 WordPress plugins, the trade-off between them may be tainted by a lot of complexity, and to facilitate Here we have collected 10 of the most essential WordPress plugins that every website needs. WordPress is one of the most widely used and best-performing content systems, and to improve this performance and get more improvement, you must have the right plugins for WordPress, and evidence of this is its use by famous sites and companies such as: US White House website. Microsoft Corporation Playstation Blog. New York Post. website Most important WordPress plugins We will present a list of the 10 most popular WordPress plugins and 90% of websites have downloaded and activated them in their control pan...
9 Hacks To Evolve A Optimistic Person That Everyone Adores
9 Hacks To Evolve A Optimistic Person That Everyone Adores No person is accurate at heart, and all you need to do is pull that high-quality and loving facet of you out. There are multiple hints which you could need to use supplied which you are searching ahead to reveal your high quality and beneficial facet. Taking this into consideration, we've taken the privilege of bringing up some such hints that can assist substantially in residing an amazing existence. Let's take a more in-depth have a take a observe those hints and hints. Desire Like something else, turning into a loving and high-quality individual needs, to begin with, having the preference of turning into one. If you aren't completely devoted to turning into this sort of individual, you might not be capable of being placed withinside the required attempt and difficult paintings into it. Lightening a robust preference to turn out to be a loving and high-quality individual needs to be your preliminary step. Realism ...
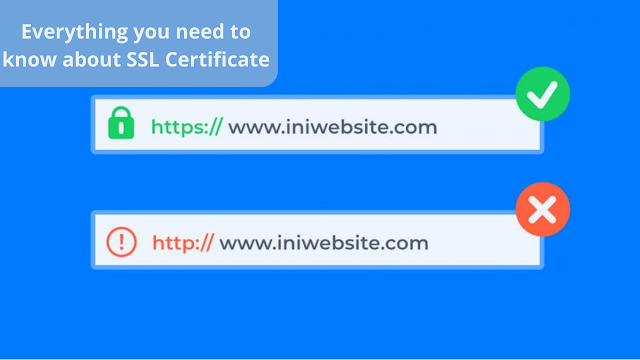
How to buy an SSL Certificate and everything you need to know about SSL Certificate
How to buy an SSL Certificate and everything you need to know about SSL Certificate The security of websites and their preservation of users' privacy has become an important aspect of the world of the Internet. It is not possible for a person to use an unsafe website. Also, the search engines have their view on this aspect, as sites that do not have an SSL Certificate do not deserve to get the first results from the search engines. In this article, we will discuss a topic that interests every website owner, which is buying an SSL certificate or obtaining it for free, to discover what it is, how it works, adjust it, and a lot of information. What is an SSL Certificate? SSL Certificate In English, the SSL Certificate is also called the Secure Connection Layer, as it creates a secure environment to connect the website to the visitor's browser, ensuring the protection of all user data that he enters into the website such as email, phone number, credit card information and other inf...